Microsoft Azure
Overview
Microsoft Azure[1] is the supported target for cloud workloads provisioned by Scaled Sense. As part of onboarding to the platform, users will be given the choice of using existing Azure Subscriptions owned by the organization or having Scaled Sense provision them. If a Microsoft Customer Agreement[2] is in place, Scaled Sense can be configured to scaffold Management Groups[3] and Azure Subscriptions in line with an adaption of the recommended guidance outlined by the Cloud Adoption Framework[4].
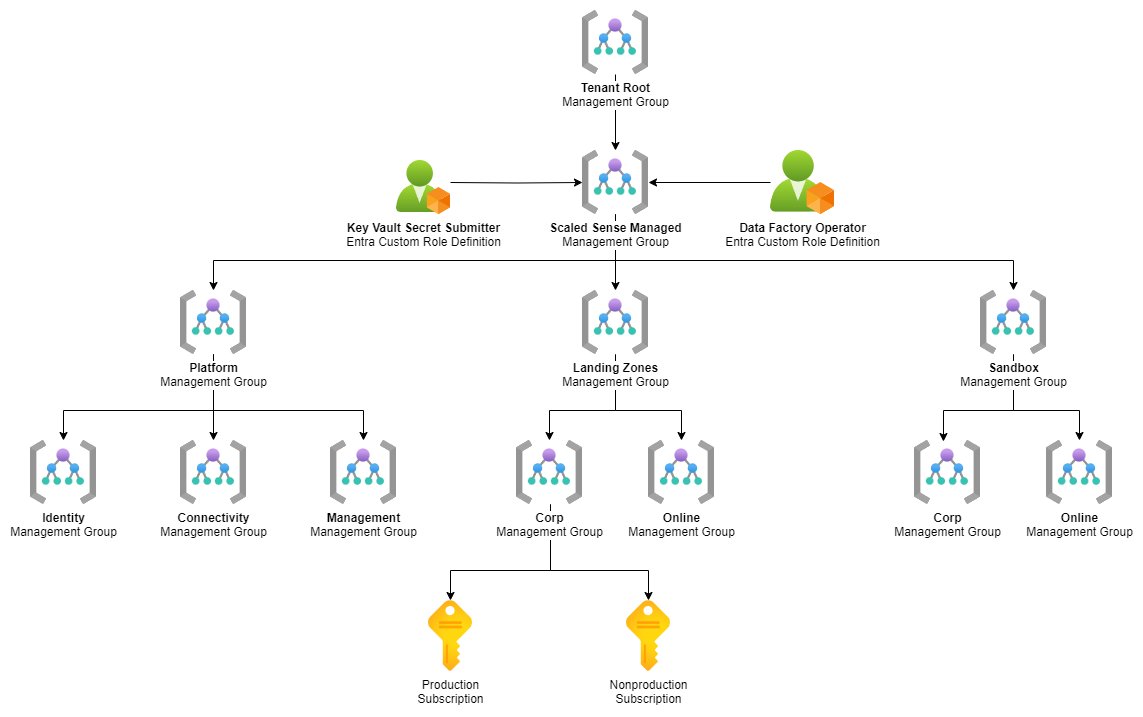
With either selection, Scaled Sense will use the configured Azure Subscriptions as the target for cloud resources provisioned by the platform.
Commonly Used Resources
- Resource Groups
- Storage Accounts
- User-assigned Managed Identity
- Azure Data Factory
- Azure Kubernetes Service
- Azure Event Hub
- Azure Frontdoor
- Azure Log Analytics
Permissions Requested
Existing Azure Subscriptions
- Owner
- Scaled Sense will create Resource Groups and assign role-based access to the Resource Groups and resources it creates.
Microsoft Customer Agreement
- (Temporary)
Management Group Contributorat the Root Management Group- Scaled Sense will create a child Management Group named
Scaled Sense Managedthat will act as the "root" for Management Groups provisioned by the platform. After the Scaled Sense Management Group has been created, the permissions at the Root can be removed, if desired.
- Scaled Sense will create a child Management Group named
Ownerof theScaled Sense ManagedManagement Group- The Scaled Sense Automation Service Principal will continue to maintain ownership of the Management Groups it provisions, which includes the
Scaled Sense Managedand all child Management Groups
- The Scaled Sense Automation Service Principal will continue to maintain ownership of the Management Groups it provisions, which includes the
Configuration Requirements
Existing Azure Subscriptions
If using existing Azure Subscriptions, it will be required to grant Owner to the Scaled Sense Automation Service Principal as part of the initial onboarding.
Microsoft Customer Agreement
- If using the Microsoft Customer Agreement option, enable Management Groups, if not already enabled.
- To perform this action, the user may need to elevate their account temporarily.
- To do this, go to the Entra ID portal > select Properties > set Access management for Azure resources to Yes, then Save.
- Note: this may take some time to propagate.
- Go to Management Groups within Azure > Overview > Start using management groups.
- If you do not see any Management Groups in the list, you will need to create a temporary management group to gain visibility to the root Management Group, if this is the case, create a Management Group with any name (this will be removed shortly).
- Assign the Scaled Sense Automation Service Principal
Management Group Contributorat the Root Management Group.- Do this by navigating back to the Tenant Root Group, then selecting Access Control (IAM) > Add > Add role assignment, and add the above role to the Service Principal.
- Enable the
Organization GovernanceService in Scaled Sense to begin the provisioning of Management Groups. - If you needed to create a temporary management group in step 1:
- Go back to Management Groups within Azure and remove that Management Group.
- Remove your user's elevated tenant permissions, go to the Entra ID portal > select Properties > set Access management for Azure resources to No, then Save.
References
- [1] https://azure.microsoft.com/en-us/resources/cloud-computing-dictionary/what-is-azure/
- [2] https://www.microsoft.com/en-us/Licensing/how-to-buy/microsoft-customer-agreement
- [3] https://learn.microsoft.com/en-us/azure/governance/management-groups/overview
- [4] https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/